Certificate Problem
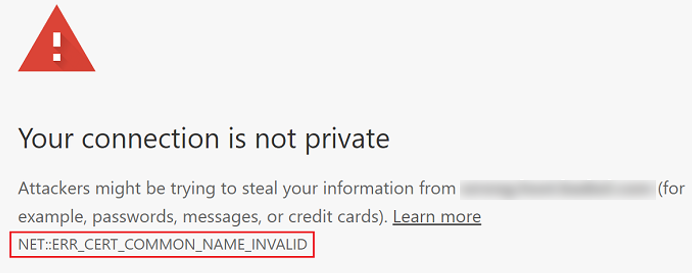
I recently had an issue after configuring Oracle HTTP Server SSL for a customer. The customer was using self-signed certificates which they managed and created themselves. I created the certificate request using the Oracle Wallet Manager as per usual and they then sent me the certificates to import into the wallet. Unfortunately the users were seeing this error when they connected to the EPM Workspace, even though the certificates were imported successfully:
Your connection is not private.
Attackers might be trying to steal your information...
NET::ERR_CERT_COMMON_NAME_INVALID
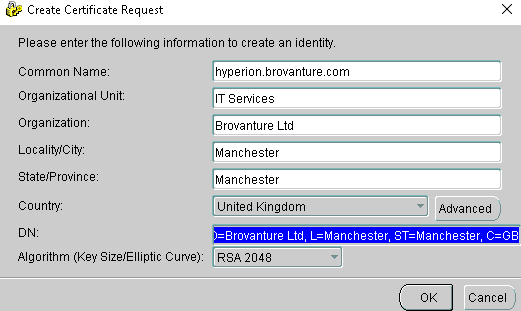
The customer determined that the issue was because the certificate didn't contain a SAN or subjectAltName (Subject Alternative Name) field. Unfortunately, the Oracle Wallet Manager UI doesn't contain a field for the SAN when you create your certificate request:
The Subject Alternative Name (SAN) is an extension to the X. 509 specification that allows users to specify additional host names for a single SSL certificate. The use of the SAN extension is standard practice for SSL certificates, and it's on its way to replacing the use of the common name.
So, how do we create a certificate request which includes the subjectAltName parameter?
Windows Command Line to the rescue! Fortunately orakpi, the command line utility for the Oracle Wallet supports the additional subjectAltName parameter. For a Oracle EPM Hyperion 11.2.x installation it can be found in the bin folder of your Oracle Client install e.g. Oracle\Middleware\dbclient64\bin
Create the Wallet Using ORAKPI
You will need to set the JAVA_HOME in your command line session before you run the command. To create the wallet using orakpi run the following command:
orapki wallet create -wallet D:\Oracle\SSL -pwd Password -auto_login
Create the Certificate Request Using ORAKPI
We can now use orakpi to create the certificate request which includes the subjectAltName parameter. First we need to get the main body of the distinguished name (DN) of the certificate request. We can use the Oracle Wallet Manager to create this for us by entering the information in a dummy certificate request and then just copying the DN string (close and don't save afterwards):
Copy the DN entry and you can paste this into your command line entry.
orapki wallet add -wallet D:\Oracle\SSL -dn "CN=hyperion.brovanture.com, OU=IT Services, O=Brovanture Ltd, L=Manchester, ST=Manchester, C=GB" -keysize 2048 -addext_san DNS:hyperion.brovanture.com
Notice the last part of the command. This is where we have added our SAN parameter, the one we couldn't add when generating using the Oracle Wallet Manager UI.
You can now go back to using the Oracle Wallet Manager UI to manage the export of the certificate request containing the SAN and import of the new certificates once you receive them. You won't be able to see the SAN entry in the UI but don't worry, it's there just not displayed.